Authors: Cristina Regueiro Senderos
Organization: Tecnalia
Cryptography is crucial in our daily lives, enabling us to trust telecommunication channels and conduct essential transactions like online shopping, finances, and healthcare. However, the internet’s short history has seen some widely used cryptographic schemas proven to be vulnerable, jeopardizing the confidentiality of information transmitted over the net. For instance, the Data Encryption Standard (DES) [1] was deemed obsolete due to the short length of its encryption keys and the rapid growth of classical computing power. Once this flaw was exposed, alternatives like the Advanced Encryption Standard (AES) [2], with longer encryption keys and better optimization in today’s hardware, became the new standard.
The challenge of protecting the information in transit arises every time we reach significant advances in computing technology. Without digging too deep into how cryptographic algorithms internally work, we can say that they generally provide confidentiality by posing a set of mathematical operations that are easy to compute in one way (encryption) but extremely difficult to solve the other way around without the exact combination of the input value (the key) used to produce the outcome. This is especially the case of public key encryption schemas, where a public key is derived from a secret peer allowing to encrypt information with the first (public) and only being able to be decrypted by the owner of the second (private). This public cryptographic schema is used not only as an encryption mechanism but also as an authentication method, a message ciphered using the private key can only be decrypted with the associated public, which demonstrates the identity of the author.
As mentioned before, cryptographic systems are always competing with computing advances, recently we have witnessed the Quantum Computing phenomenon, and this groundbreaking technology is attracting research efforts in order to provide a complementary solution to classical computing with unprecedented expectations about its possibilities. Although the current quantum machines are in a race to achieve stable and feasible results in their qubit implementations, there are already new “quantum algorithms” implementations specifically designed to embrace the quantum advantage over the classic alternatives to solve specific mathematical problems used by public key algorithms. To address the issue, the cryptographic community is already working to provide alternatives to these algorithms with more resilient alternatives to this level of computing power.
NANCY project identifies the need to push forward the state-of-the-art privacy-protecting technologies in B5G infrastructures, that is why, in addition to the Post Quantum Cryptographic algorithms, other Quantum Safe methods to safeguard information privacy have been considered in NANCY. More specifically, a set of experiments with Quantum Key Distribution (QKD) are taking place.
QKD is a novel technique to protect against eavesdroppers a fully randomly generated secret key between two stations geographically distant. This method uses the same Quantum Physics that poses a threat to the current cryptography in order to provide a valid solution to this issue. These activities involve the use of dedicated hardware with specific Quantum properties in order to produce a continuous flow of secret key material to be securely sent over optical fibres to the destination to be consumed in a decryption operation.
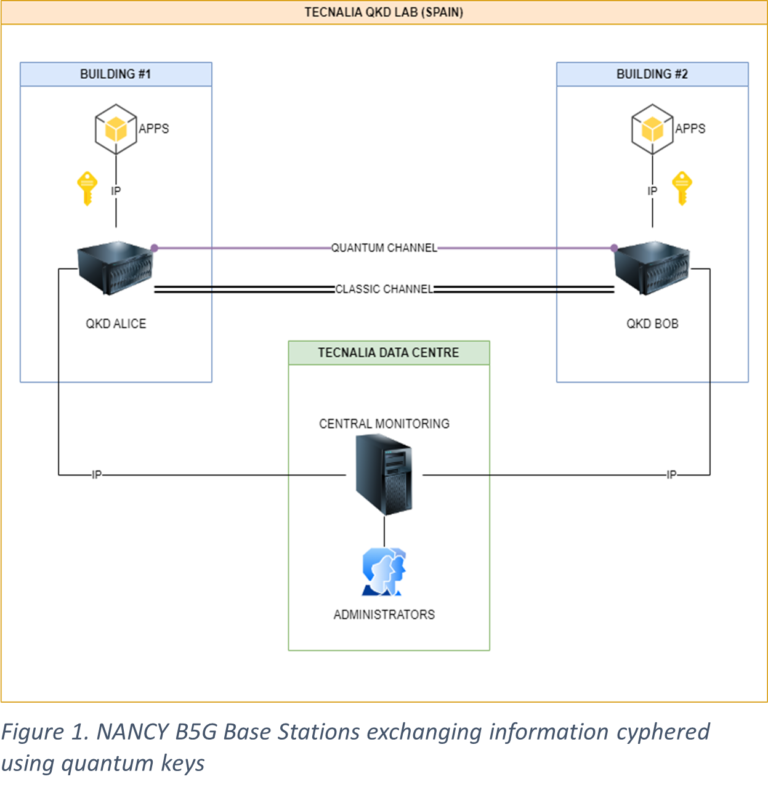
QKD takes advantage of the uncertainty principle and no-cloning theorem of quantum physics. Essentially, a random number generator powered by quantum operations originates a random key that is later processed by some optical components such as intensity and polarization regulators to produce a weak laser pulse of coherent light attenuated to near a single photon. This pulse is transmitted through a standard telecommunications fibre to a receiver device as can be seen in Figure 1. Both sides of the link must be physically connected with two dark fibres at least. The first is known as the quantum channel and is where the attenuated laser pulses will travel, the other, known as classic, transports classic optical signals needed by the peers to support a public information exchange needed to reach an agreement about the key transferred by the quantum link.
Because of quantum physics, if someone is able to eavesdrop on the photons of the quantum link without the polarization settings used in the source to encode the information, the outcomes turn into a piece of completely random and unrelated information, furthermore, the destination device would detect in its decoding operations that the Quantum Bit Error measured in its side is too high, alerting about an eavesdropping presence and cancelling the information exchange immediately.
As this secret key exchange relies on the uncertainty principle (the only presence of an observer produces a disturbance in the system), the computing assumption of the attacker is no longer an issue. This allows us to achieve unconditional security in communications when this key exchange is used in combination with strong symmetric cyphersuites. The QKD technology is probably one of the most mature branches of the current quantum technologies.
However, the current technical limitations of current commercial hardware present some challenges to use cases as NANCY proposes. Parameters like key transfer rate and latency impact on communications must be evaluated to determine if B5G network backbones can benefit from these advantages. NANCY QKD experiments are testing and taking different measures for different transmission lengths with TECNALIA QKD equipment and fibre optics simulating 5G Base Station information exchange. Table 1 presents the testing scenarios proposed in this approach. The results of these testing environments will be detailed in the upcoming deliverable D5.1.
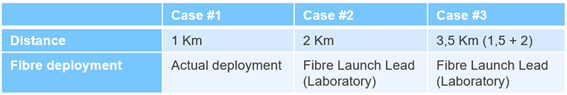
Table 1 Test cases to experiment
References
| [1] | E. Barker and A. Roginsky, “Transitioning the Use of Cryptographic Algorithms and Key Lengths,” No. NIST Special Publication (SP) 800-131A Rev. 2 (Draft), 2019. |
| [2] | M. E. Smid, “Development of the Advanced Encryption Standard,” Research of the National Institute of Standards and Technology, vol. 126, no. 126024 , p. 18, 2021. |